The app is called ESET USSD Control. According to Tibor Novosad, Head of Mobile Applications Section at ESET: “ESET USSD Control is an application that allows the user to check potentially malicious phone numbers (USSD codes) before they are dialed (executed) by the default phone dialer. ESET USSD Control will block malicious websites [that abuse USSD codes] as well. Checking for malicious codes before they are executed, ESET USSD Control makes sure all data on an Android phone stays safe.”
How does ESET USSD Control work?
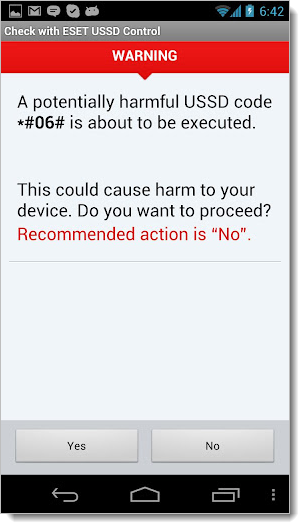 The
app displays a warning window each time a malicious USSD code is found,
blocking the execution of the command, as seen in the screenshot on the
right.
The
app displays a warning window each time a malicious USSD code is found,
blocking the execution of the command, as seen in the screenshot on the
right.In order to protect your Android smartphone from USSD attacks, you have to make sure that ESET USSD Control is set as the default dialer. Here’s how:
- Download ESET USSD Control from Google Play and install on your Android phone.
- Use your Android phone to visit our test page: http://www.eset.com/tools/ussdtest (note that this only contains a checker and will not make changes to your phone).
- When prompted to complete the action, select “Use by default for this action” and select ESET USSD Control.
We hope this app will help keep your Android safe. We’re pleased to make this available free to the Android community as part of our continuing effort to support the Android ecosystem and to empower users to stay safe on their mobile devices.
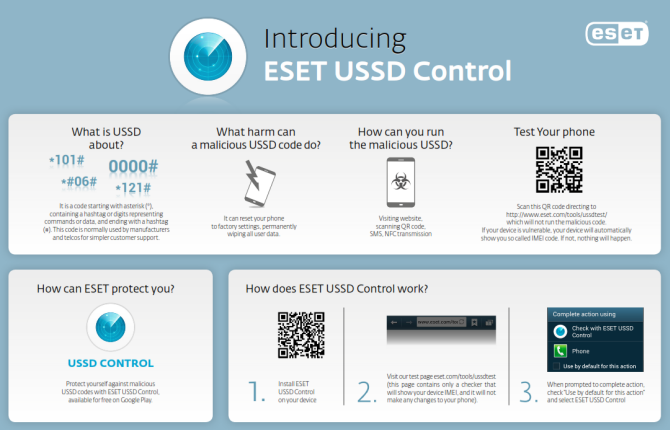
The Android USSD Vulnerability
USSD is a code used by phone manufacturers and carriers for simple customer support. The letters stand for Unstructured Supplementary Service Data (USSD). The code starts with an asterisk (*) and continues with hashtags or digits representing commands/data, then ends with a hashtag (#). By entering these codes on your phone you can, for example, see your device’s IMEI (International Mobile Equipment Identity). The USSD code for this is *#06#. Other codes reveal different information or carry out actions, like a device reset.The potential exists for a web page to instruct your phone to load a “tel:” URI (uniform resource identifier) with a special factory reset code inside an iframe. As Lucian Constantin at ComputerWorld reported, this attack was described by Ravishankar Borgaonkar, a research assistant in the Telecommunications Security department at the Technical University of Berlin, who demonstrated the remote data wiping attack during the Ekoparty security conference in Buenos Aires, Argentina.
These malicious iframes could be placed on hacked websites or specially designed sites. As you probably know, there are numerous ways to trick your smartphone into going to a website, like QR codes or NFC chips (as my colleague Stephen Cobb illustrated in a short video). With ESET USSD Control on your Android you won’t need to worry that such tricks will be used to wipe your phone via USSD codes. For more about this problem, and ESET’s solution, check out the infographic (click for larger view):
No comments:
Post a Comment